Facebook is one of the biggest social media platforms in the world. It is owned by a parent company named “Meta”. These days many people have a Facebook account or profile. Mostly it is used for communicating, chatting, keeping updated with friends, and families, and marketing. Some people also use it to read news and stay updated on different pages. The platform has quite good security measures for account safety but people’s accounts do get hacked. There are many reasons for accounts getting compromised. It can be hacking, phishing, viruses, and many other reasons. As the number of users is rising, problems are also rising. So here we are going to provide a guide on how to recover Facebook account.
There are many people, software, applications, and viruses that want to access your social media account. These parties can maliciously access your online accounts to get information, blackmail you, defame you, and possibly take your financial information. Regardless of the motive, a victim of cybercrime faces a lot of stress.
Facebook account hacking and recovery can sometimes cause serious troubles. Many users face such issues these days. Account compromise can be an attack, mistake, phishing, or the cause of a virus. According to the cybercrime investigation department of Nepal Police, Facebook or social media-related crime is one of the biggest cybercrime in Nepal. In order to tackle such issues, many countries have strict rules regarding cybercrime but these things still happen. So in this article, we will provide help on how to recover hacked Facebook account and how to secure them.
Also Read: Cybercrime Penalties in Nepal
Possible Causes of Facebook Account Hacking and Compromises
There are many possible causes of the Facebook account getting hacked or compromised. People might hack others’ accounts to get information, defame them, and take over pages or businesses. There can be many reasons for activity. It is hard to list all of them but there are some specific ways that people’s accounts get hacked. We shall discuss them because it will help you to understand and realize the cause.
Phishing
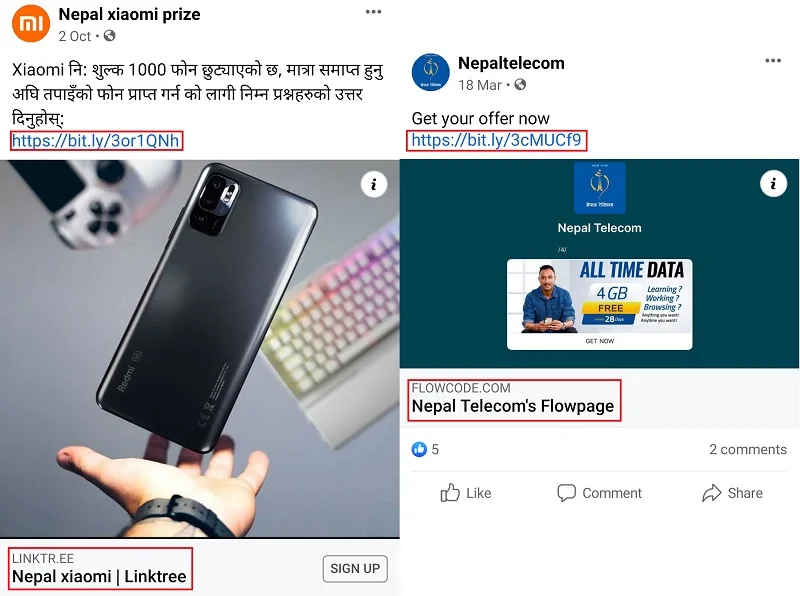
It is a very famous way to exploit someone’s credentials. Phishing is actually done using a fake page that resembles the look of the original website. People are tricked into believing that the fake page is the original one. Thus when a user provides their credentials, card information, or login information with their password and username, everything is captured by the phishing site. Phishing of credit cards and online banking information is also very popular, so be careful.
People with malicious intent create a Facebook page with the exact name of a famous brand or company. They make the look of the fake page just like the original one by using design, images, and covers from the original page. Then they post attractive offers such as giveaways and free gifts. The fake pages even boost those posts to attract people. So when people click on those links, people are shown a fake Facebook login page and they are asked to log in. This is where people fall into the trap. People give their credentials and the criminals record them. Phishing page links can also come through messages and emails.
First of all, Facebook should have tight scrutiny on such pages with the same names as popular brands. Second of all, they should have tighter scrutiny on boosted posts or ads. Thirdly people should not believe in unbelievable posts of gifts and giveaways. Even after clicking the link, one should check the URL or link of the page. The simplest safest way is not to enter your login information anywhere except the Facebook app or website.
Keyloggers
Keylogging is the method of targeting a user’s login information using spy software. The keyloggers are actually a virus and they can see what you are typing. If you are careful you can prevent them. Keylogger malware usually spreads through tampered software, dubious web pages, unsafe files, links, cracks, etc. They can come attached with pirated software or they may install themselves silently when browsing a dangerous website. When a keylogger is installed, it is difficult to find without antivirus software or a firewall.
Keyloggers record what you type using the keyboard. Therefore they can record the texts and login credentials. The victims usually don’t know that the keylogger is active and when they type credentials using the keyboard, all the information is sent to the hackers.
Therefore always use a firewall and antivirus on your computer. Update your operating system regularly and update your antivirus or at least Windows Defender. In the case of mobile, use the latest security patch and OS update. Never use cracked APK files. Most importantly, never use social media and banking websites on someone else’s or suspicious devices.
Also Read: Fake Facebook friends scam and fraud in Nepal
Social Engineering
Social engineering is the most sophisticated way to get someone’s credentials. It is basically psychological manipulation that is done to trick someone. These people get the confidence of target, study people, and get the credentials. The culprits can sometimes be people close to the victim because they know a lot about them. For example, someone is a fan of a football club and a player. Then there is a high chance that the user will have a password related to those two topics. Hackers try the possible keywords around those objects and get their way in.
Many social media sites and websites also have password recovery options using secret questions. Social Engineers get close to you and study you. Therefore they get enough information to answer the security questions and change your password. So be careful when someone is trying to get detailed information about your life.
Compromise of Stored Passwords
These days almost everyone uses password managers in browsers, mobile apps, plugins, and special software. This is because we have to use strong, long, and complex passwords but they are hard to remember. We can write them down on a piece of paper and store them safely but it is hard when we need to reenter them again. So most users save the passwords on browsers or password managers. These things are quite safe but when they are compromised all of your passwords are compromised. If any person gets access to the stored passwords then that can lead to social media accounts getting hacked.
It is very important to keep all your passwords safe. Only store passwords on your computer and smartphone. Use biometrics security options in password managers. Moreover, use two-factor authentication (2FA) for better security.
Brute Force Attack
These days systems are smart and they block the account when someone tries to log in with multiple wrong passwords. However, brute force attack is a popular technique for hackers. It is a type of attack where a computer is used to crack the system password. It is done by trying and matching every possible character. All letters like alphabets, numbers, and special characters are tested. This can take a huge amount of time considering the password length and the computer’s power. This is very hard for normal people.
Steps to recover Facebook account: Things to do for Facebook recovery
Take rapid action as soon as you find out that your Facebook account has been hacked or compromised. There can be two cases of hacking. One is the case where a user loses access to the account. The password, email address, and phone numbers are all changed. Then there is a second case where a malicious party may have gained access to your account but you might not know about it. Such cases have been reported in Nepal where hackers gain access to someone’s account and they contact friends to transfer money through mobile wallets.
There are many ways to recover a Facebook account and they can be challenging too. To start the recovery process, use the device that you always use for browsing Facebook. For example, it can be your personal laptop or mobile phone. Also, it would be better if you use the network of the same location such as home WiFi. Such data helps the support engineers to get confidence that you are the true owner because those data will match previous logins.
a) Recovery with notification email
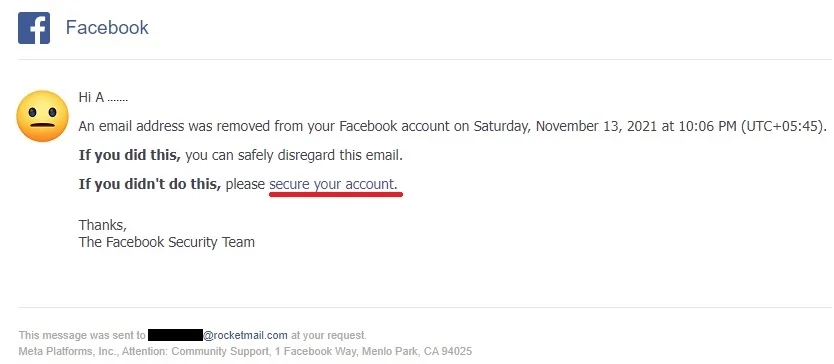
Whenever someone changes the default email address associated with Facebook or any social media account, a notification email is sent to the older address. This email has a special link where the owner can report the unauthorized change. So if your email address was changed then find the old notification in your inbox and spam folder. There might be a link where you can report the change and get your account back. However, if the email ID is intact, then you can simply click on “Forgotten password?” on the login page and recover the password.
b) Recover Hacked Facebook Account Without Email And Phone Number
This is a complex process of account recovery. If the hacker has changed the email, password, and phone number then you have to follow the recovery process thoroughly.
- Search for “Hacked Wizard Page” in Google and click on the link by checking the URL.
- Follow the steps provided according to your situation. You can use the recovery tool to report your account, a friend’s account, or a fake one created using your name, photos, or details.
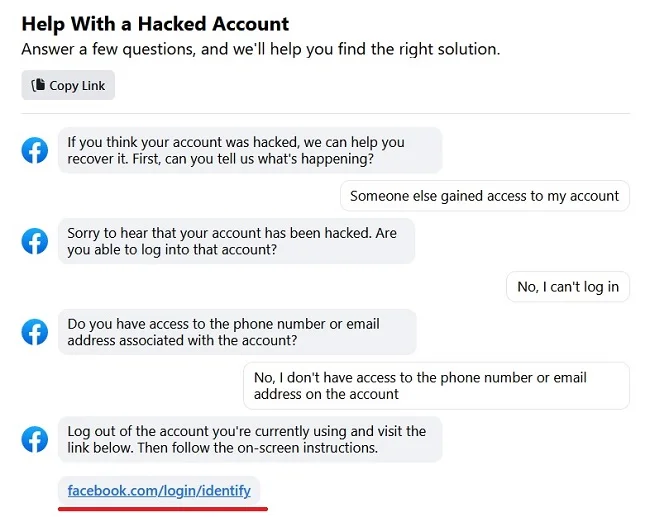
- After you choose the option which says that you don’t have access to your old email address and phone number, the tool directs you for identity verification. The link from “facebook.com/hacked” also sends users to the same identity verification page.
- Search for your account using your current name, profile URL, old email address, or phone number. The hacker might have changed the name so enter the current name your profile shows. Also to get the profile URL, use your browser history or a friend’s account.
- Facebook then asks you to recover using codes that are sent to your email ID and phone number. If you have access to your old email address, you might get the option to recover it. However, things get difficult when you don’t have access to your old email ID. In some cases “Account access not possible” will be shown.
- If you can’t recover from the old email address and when Facebook says that account recovery is not possible or “Account access not possible”, click on the link that indicates more ways to access your account.
- Facebook usually presents a way to recover the account through ID verification. The verification link is generally sent using email and may be also found on the website.
Identity Verification
Facebook requires users to verify their identity when an account is locked. Usually, when we report a hacked account or go into the recovery process, the account can get locked. So when we can’t perform password recovery using normal methods, the remaining option is identity verification. Facebook or any other company needs to confirm that the user requesting the recovery is the real owner. This process usually requires ID card documents for verification.
It is best to upload a government-issued ID like citizenship, driver’s license, passport, etc. If you don’t have a government document then you can upload two ID cards that match the user’s name, DOB, and matching picture. The company has a list of Facebook accepted government and non-government IDs in their help section. You can send those documents to the company through the verification form on the website or through the mail. Sometimes the staff also provide an option to send documents directly through email.
The things you need for the recovery process are your name, date of birth, ID, and Facebook profile or timeline URL. For many people, a passport, driver’s license, voter ID, college ID card, library card, etc can be easier options for ID. It is very important that the documents clearly show your name, date of birth, and photo. It is also due to this reason, why you should always use your original name, date of birth, and photo in your social media profile. The original information makes it easy for staff to verify the information.
c) Ways to recover Facebook account through friends and family
Ask your family members or friends to help you in the recovery process. You can report the profile for hacking and proceed to recover from a friend’s profile. It is actually not necessary for the family member or any person to already be a friend of you on the compromised account or profile.
- Find your profile on Facebook and open it.
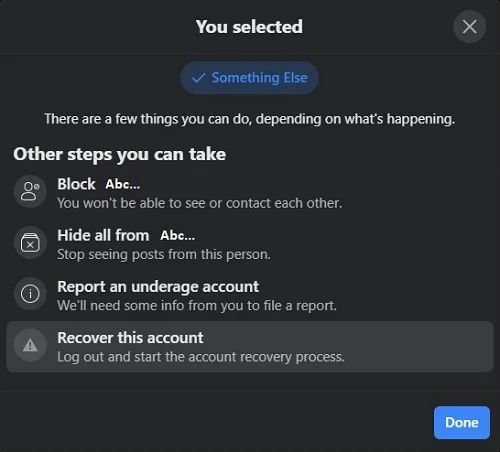
- Click the three dots on the profile and click on “Find support or report profile”.
- Search for the option saying “Recover this account”. That can be in the section saying “I can’t access my account” or “Something Else”.
- It can also allow you to provide a new email address for recovery.
- Then you might again be asked to verify the identity. Sometimes Facebook might even request a user to upload a photo of an ID card next to the user with the help of a webcam.
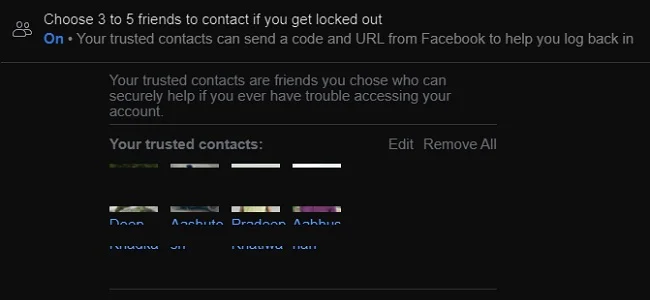
d) Trusted Contacts
Users can also recover hacked Facebook accounts through friends. It is an account recovery feature that was introduced in 2013. This method is only applicable to users who have already set some Facebook trusted contacts in the profile. Facebook allows a user to choose 3 to 5 trusted contacts or friends. These contacts can help you log in to your account when there is a problem. Trusted contacts can send special URLs and codes for login at the time of login issue.
If you have set up trusted contacts, then you can choose the option of password recovery using the contacts. All you need to do is send a link or ask your friends to open a specific link. They receive a code and you need to ask them for that. Provide the codes sent to your trusted contact through the form. Then you can proceed with Facebook password recovery and restore your account after verification. This method can also easily recover your profile.
Safety Tips: How to make your Facebook account secure?
The first and most important thing to make sure of every time you use a device is security. Always use your own smartphone, laptop, tablet, or computer for accessing social media accounts. Secondly, make sure you are on a secure private connection. Thirdly don’t attempt to recover passwords if you suspect viruses, phishing, keylogging, and device compromise. It is very essential that you stop using the old device to reduce further damage. This is because there still might be viruses and keyloggers. If you are going to the police to register a cyber crime complaint, then it is better to leave the device as it is. Formatting and resetting the device might tamper and weaken the investigation.
However, if you are not going to register a legal complaint, then format the device and change other saved passwords. Start the Facebook account recovery process as explained in this article. In order to be safe from hacking attempts and malicious activities, try to follow some of our recommendations.
- Never click suspicious links sent to you by anyone. Sometimes malicious links spread automatically to all victim’s contacts or friends. Therefore message the friend or family again and ask about the link. If they confirm then you can process it. Always open links from trusted and authentic sites or Facebook pages.
- Be very careful while opening your accounts from public places like cyber cafes and public WiFi.
- Use genuine software and don’t use cracked apps
- Use longer passwords with a combination of random alphabets, numbers, and special characters.
- Don’t use the same password for all websites and apps.
- Use two-factor authentication (2FA).
Take expert and legal help when needed
There can be cases of defaming, blackmailing, scamming, and fake photo and video circulation. There can also be cases of money or business page hacking. In such cases, one should use expert and legal help. Such big issues require the help of police and cybercrime experts. Government agencies like the police and criminal investigation departments have more power. They can help much better in the case of serious Facebook account hacking and profile recovery. They can track IP addresses, triangulate the cell phone and catch the culprit. Government agencies can also contact the offices of social media companies abroad and ask them for assistance. So always take legal and expert help when needed.
First Published: Oct 9, 2015 (Updated: When Required)